
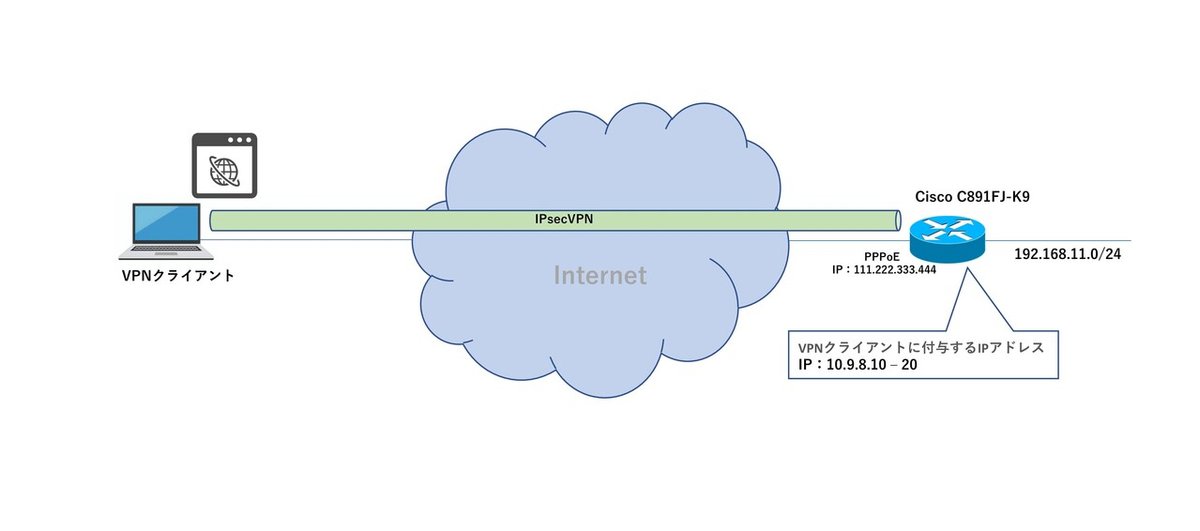
Shrew Soft VPN Clientを使用してCiscoにリモートアクセスVPN接続する
◆ Cisco C891FJ-K9 の変更前 config
hostname R1
no aaa new-model
interface Loopback0
ip address 111.222.333.444 255.255.255.255
interface GigabitEthernet0
switchport access vlan 10
no ip address
interface GigabitEthernet8
description ### to Internet ###
no ip address
duplex auto
speed auto
pppoe enable group global
pppoe-client dial-pool-number 1
interface Vlan10
ip address 192.168.11.1 255.255.255.0
ip nat inside
ip virtual-reassembly in
ip tcp adjust-mss 1356
interface Dialer1
mtu 1454
ip unnumbered Loopback0
ip nat outside
ip virtual-reassembly in
encapsulation ppp
dialer pool 1
dialer-group 1
no cdp enable
ppp authentication chap callin
ppp chap hostname user@host.net
ppp chap password password1234
ip nat inside source list 101 interface Loopback0 overload
ip route 0.0.0.0 0.0.0.0 Dialer1
ip ssh version 2
dialer-list 1 protocol ip permit
access-list 101 permit ip 192.168.11.0 0.0.0.255 any
◆ 投入 config
aaa new-model
aaa authentication login VPNAUTHE local
aaa authorization network VPNAUTHO local
username remoteuser1 password userpass123
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp keepalive 30 periodic
crypto isakmp client configuration group VPNCLIENT
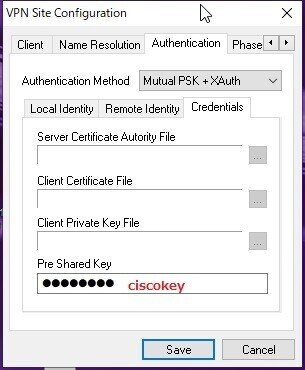
key ciscokey
pool EZREMOTE
save-password
crypto isakmp profile VPN-PROFILE
match identity group VPNCLIENT
client authentication list VPNAUTHE
isakmp authorization list VPNAUTHO
client configuration address respond
crypto ipsec transform-set REMO-IPSEC esp-3des esp-md5-hmac
crypto dynamic-map REMO 1
set transform-set REMO-IPSEC
set isakmp-profile VPN-PROFILE
crypto map EZVPN 1 ipsec-isakmp dynamic REMO
ip local pool EZREMOTE 10.9.8.10 10.9.8.20
interface Dialer1
crypto map EZVPN
ip access-list extended 101
5 deny ip 192.168.11.0 0.0.0.255 10.9.8.0 0.0.0.255
◆ 変更後 config
hostname R1
aaa new-model
aaa authentication login VPNAUTHE local
aaa authorization network VPNAUTHO local
username remoteuser1 password userpass123
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp keepalive 30 periodic
crypto isakmp client configuration group VPNCLIENT
key ciscokey
pool EZREMOTE
save-password
crypto isakmp profile VPN-PROFILE
match identity group VPNCLIENT
client authentication list VPNAUTHE
isakmp authorization list VPNAUTHO
client configuration address respond
crypto ipsec transform-set REMO-IPSEC esp-3des esp-md5-hmac
mode tunnel
crypto dynamic-map REMO 1
set transform-set REMO-IPSEC
set isakmp-profile VPN-PROFILE
crypto map EZVPN 1 ipsec-isakmp dynamic REMO
interface Loopback0
ip address 111.222.333.444 255.255.255.255
interface GigabitEthernet0
switchport access vlan 10
no ip address
interface GigabitEthernet8
description ### to Internet ###
no ip address
duplex auto
speed auto
pppoe enable group global
pppoe-client dial-pool-number 1
interface Vlan10
ip address 192.168.11.1 255.255.255.0
ip nat inside
ip virtual-reassembly in
ip tcp adjust-mss 1356
interface Dialer1
mtu 1454
ip unnumbered Loopback0
ip nat outside
ip virtual-reassembly in
encapsulation ppp
dialer pool 1
dialer-group 1
no cdp enable
ppp authentication chap callin
ppp chap hostname user@host.net
ppp chap password password1234
crypto map EZVPN
ip local pool EZREMOTE 10.9.8.10 10.9.8.20
ip nat inside source list 101 interface Loopback0 overload
ip route 0.0.0.0 0.0.0.0 Dialer1
ip ssh version 2
dialer-list 1 protocol ip permit
access-list 101 deny ip 192.168.11.0 0.0.0.255 10.9.8.0 0.0.0.255
access-list 101 permit ip 192.168.11.0 0.0.0.255 any
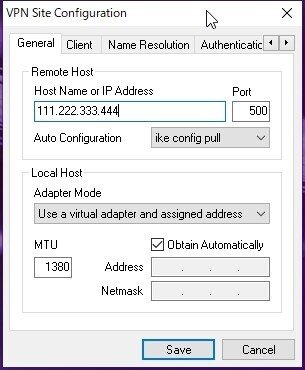
◆ Shrew Soft VPN Client の設定
https://www.shrew.net/download/vpn
からダウンロードした「2.2.2-release」を使用する。








#追記
#syslog メッセージをイネーブルにする場合
#以下のconfigを追加
crypto logging ezvpn
この記事が気に入ったらサポートをしてみませんか?
